With CloudHub 2.0, applications are deployed in public spaces or private spaces. Private space isolates the applications deployed, and different network customizations can be done within the private space. Earlier in CloudHub 1.0, DLB used to be configured to balance the incoming load along with configuring the custom/vanity domain instead of using *.cloudhub.io
We can configure vanity/custom domains in the private space, avoiding accessing the applications through the default *.cloudhub.io domain. Configuring the custom domain will require the public certificate and the private key as a prerequisite.
Generating the self-signed public certificate and the private key 🔗
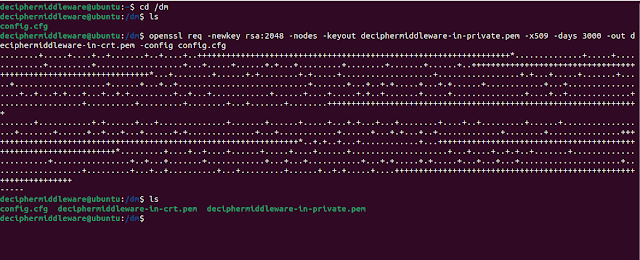
For simplicity, we will try to create certificates for the wildcard domain. To generate the self-signed public certificate and private key, we will require OpenSSL.
1. Create a config file as below, name it config.cfg , and change the values as per the domain details.
[ req ]
default_bits = 2048
distinguished_name = req_distinguished_name
prompt = no
[ req_distinguished_name ]
countryName = IN
stateOrProvinceName = Punjab
localityName = Amritsar
organizationName = DecipherMiddleware
commonName = *.domain.com
2. Run the below command through the terminal. Currently, expiration is set to 3000 days.
openssl req -newkey rsa:2048 -nodes -keyout deciphermiddleware-in-private.pem -x509 -days 3000 -out deciphermiddleware-in-crt.pem -config config.cfg
This will generate 2 files: a public certificate and a private key. These 2 files will be used in the later stage.
Steps: Anypoint Platform 🔗
Let’s now log in to the Anypoint Platform.
1. Go to Runtime Manager and click private spaces.
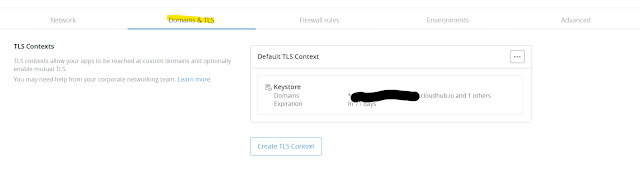
2. Select the private space, where the custom/vanity domain needs to be configured. Click on Domains & TLS.
3. Click on Create TLS Context.
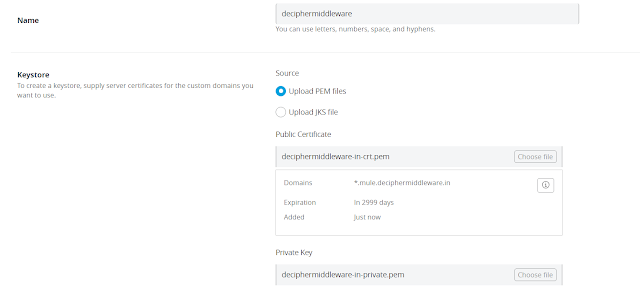
4. Enter the name for configuration. Upload the public certificate and the private key created in the previous steps. Certificates have been configured to have domains as *.mule.deciphermiddleware.in
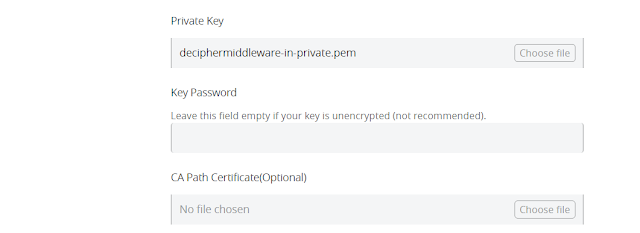
5. Enter the keystore password, if the keystore was encrypted. If you have CA signed certificate upload that as well.
6. Click on Create TLS Context.
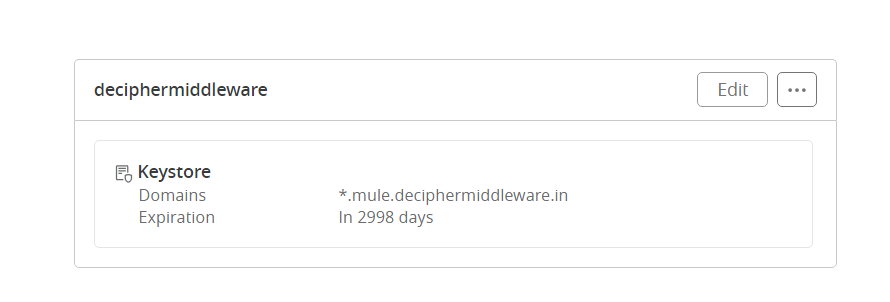
7. A new TLS context will be created as below.
Let’s configure an application to use the newly configured custom domain.
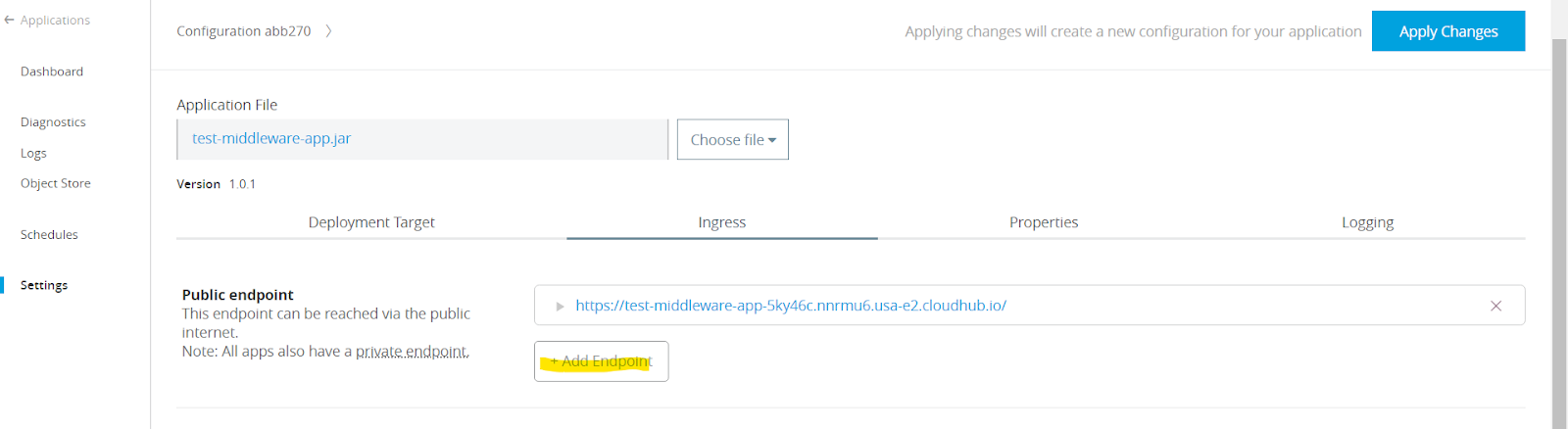
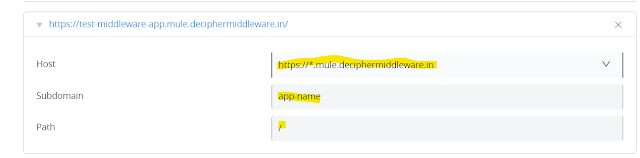
8. Open any CloudHub 2.0 application deployed in the Private Space. Go to settings. Click on Ingress , and click on Add Endpoint.
9. Change the host to the custom host configured. For now, leave the remaining fields as is. Click on Apply Changes. This will deploy the application with a new configuration as defined by the deployment model.
10. Before using the custom domain, make sure the DNS record with the following values is being configured.
| Record Type | CNAME |
|---|---|
| Host (or Name) | wildcard or wildcard with subdomain (*.mule used in the current example) |
| Value (or Content) | Private Space default hostname |
Validate if the DNS record is working 🔗
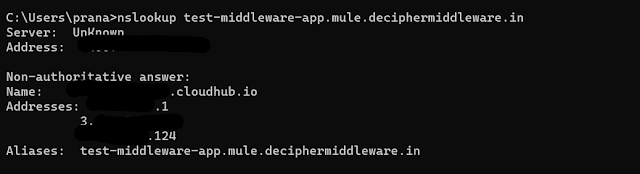
The below command can be used to check if the DNS records are configured properly.
nslookup
If private space static IPs and default hostname are visible as output, then configuration is proper and DNS routing is working as expected.
Apps can be accessed using the custom/vanity domains.
References 🔗
https://docs.mulesoft.com/cloudhub-2/ps-config-domains#before-you-begin
Please share your valuable feedback 😊😊😊